In an increasingly digital world, maintaining online privacy has become more crucial than ever. With threats like cyberattacks, and invader tracking techniques on the rise, a lot of individuals and organizations are turning to proxy solutions as a powerful solution. These tools not only help hide user identities and also provide a variety of extra benefits that enhance security and mitigate risks during internet use. Grasping what a proxy server is and how it operates can allow you to take control of your digital footprint in a better way.
Proxy servers function as intermediaries between your device and the internet, allowing you to navigate the internet anonymously and bypass geographical restrictions. Their flexibility means they can be employed for many purposes, from enhancing personal privacy while surfing the web to strengthening business cybersecurity efforts. As we investigate the basic principles of proxy servers, we will delve into the other features they offer, such as enhanced productivity and the capability to access location-restricted content. Throughout this article, we will uncover why proxy servers are frequently viewed as the best tool for achieving true online privacy.
Comprehending Proxy Servers and Their Functions
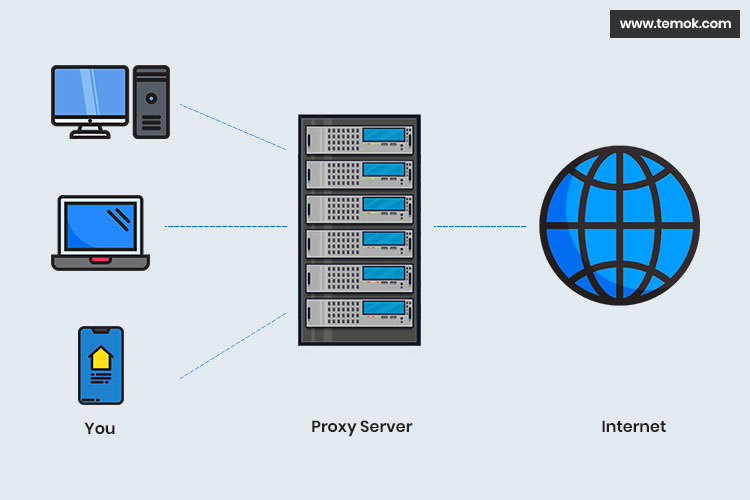
Proxy servers act as go-betweens between your system and the internet, managing demands for content including websites. When you use a proxy server, the requests made by you are sent to the server first, which then forwards them to the intended URL. This procedure conceals your IP address and can enhance your online privacy and protection. By sending your online activity through a proxy, you can stop sites from observing your data and address.
Different types of proxy servers can be found to satisfy various needs, including HTTP, SOCKS, and transparent proxy servers. Every type has its own functionality and use cases. For instance, HTTP proxies are ideal for surfing the web, while SOCKS proxies support all kinds of internet traffic, making them more versatile. It’s vital to pick the suitable type depending on your needs, whether general browsing, content streaming, or data scraping.
Besides boosting privacy, these servers offer gains such as enhanced security against online threats. They can help screen harmful content and guard your personal identity from potential hackers. Nonetheless, not all proxy servers are equal in effectiveness, and their performance can fluctuate. Knowledge of the distinct features and constraints of proxy servers enables users to make informed decisions about their internet navigation approaches.
Benefits and Drawbacks of Proxy Usage
Using proxy servers can significantly enhance online privacy by masking a user's IP address, making it harder for third parties to track internet usage. This added layer of anonymity allows individuals and businesses to browse the internet with a reduced risk of being monitored. Additionally, proxies can help bypass geo-restrictions, enabling access to content that may not be available in specific regions. Omeka.net is particularly beneficial for researchers and marketers who need to gather data from various locations.
However, there are also risks associated with using proxy servers, especially free ones. Many free proxies can compromise users' security by logging data or injecting ads, which poses significant threats to privacy. Additionally, these proxies may have slower connection speeds or be unreliable, which can disrupt browsing or streaming experiences. It's vital for users to thoroughly vet any proxy service before proceeding to ensure they are not jeopardizing their security for the sake of convenience.
Moreover, while proxies provide anonymity, they do not inherently encrypt data the same way a VPN does. This means that even though your IP address might be hidden, your data may still be vulnerable to interception. Thus, users should carefully consider their needs and the level of security required when choosing between proxy servers and other solutions like VPNs, depending on the sensitivity of the information being accessed or transmitted online.
Proxy for Specific Applications
Proxies are increasingly utilized across multiple sectors, each benefiting from the enhanced anonymity and security they provide. Businesses are leveraging proxies to bolster their cybersecurity measures. By routing employee internet traffic through proxy servers, companies can monitor and control the information exchanged, avoiding potential breaches and ensuring sensitive information remains protected. This approach not only safeguards company data but also reduces risks associated with employee misconduct online.
In the realm of content streaming, proxies serve as a beneficial tool for accessing geo-restricted services. Individuals can bypass regional restrictions on platforms like Netflix and Hulu by linking through a proxy located in a permissible country. This not only expands content availability but also improves the overall streaming experience. However, understanding the details of proxy types is important, as certain proxies may be more effective in eluding detection by streaming services than other types.
Furthermore, gaming enthusiasts are tapping into proxies to improve their online experiences. By employing proxies, gamers can reduce latency, circumvent IP bans, and access region-locked games. This has become essential for competitive players who need every edge possible in fast-paced environments. Additionally, with dedicated gaming proxies available, users can enjoy smoother gameplay while preserving privacy, ultimately leading to an improved gaming experience.
